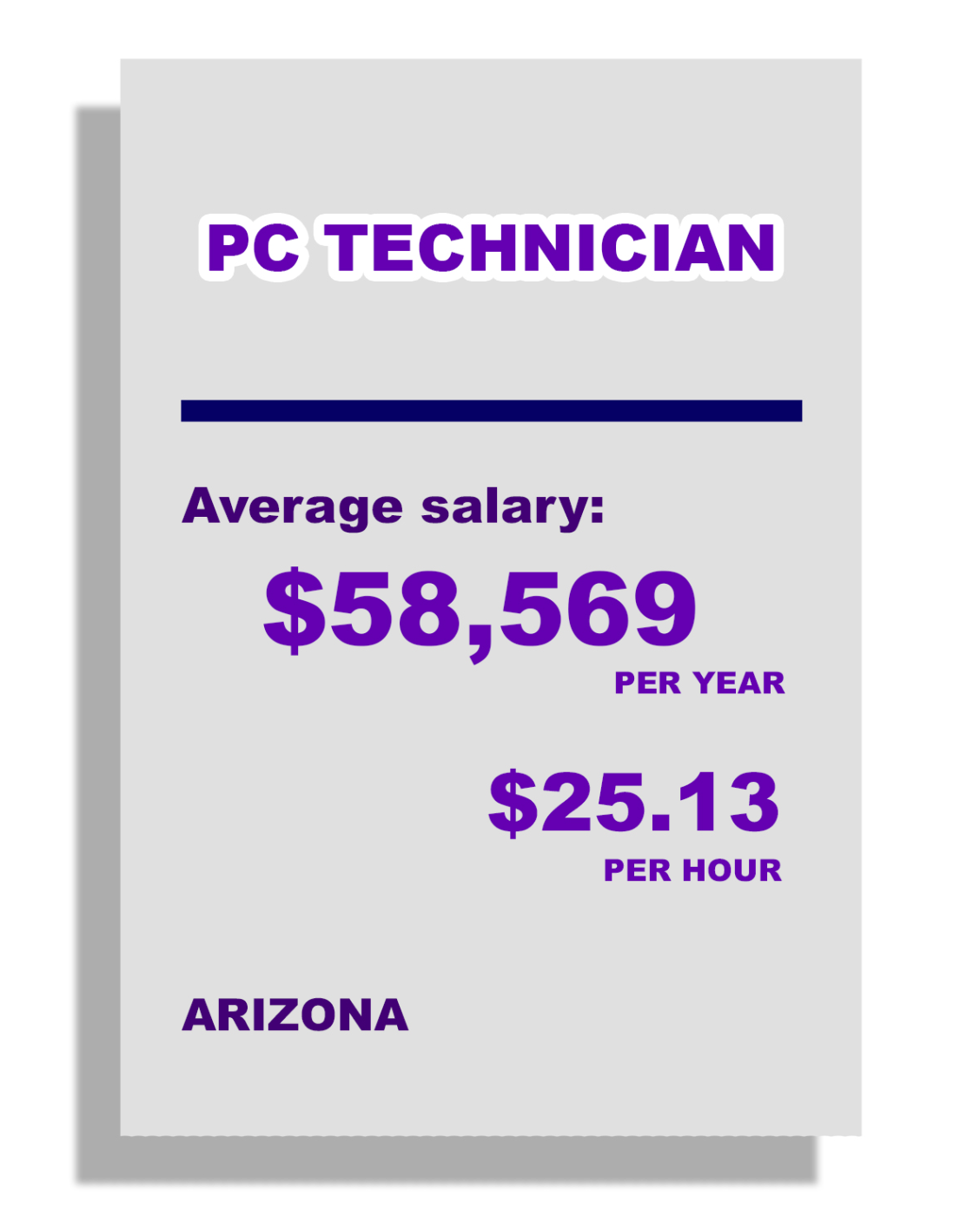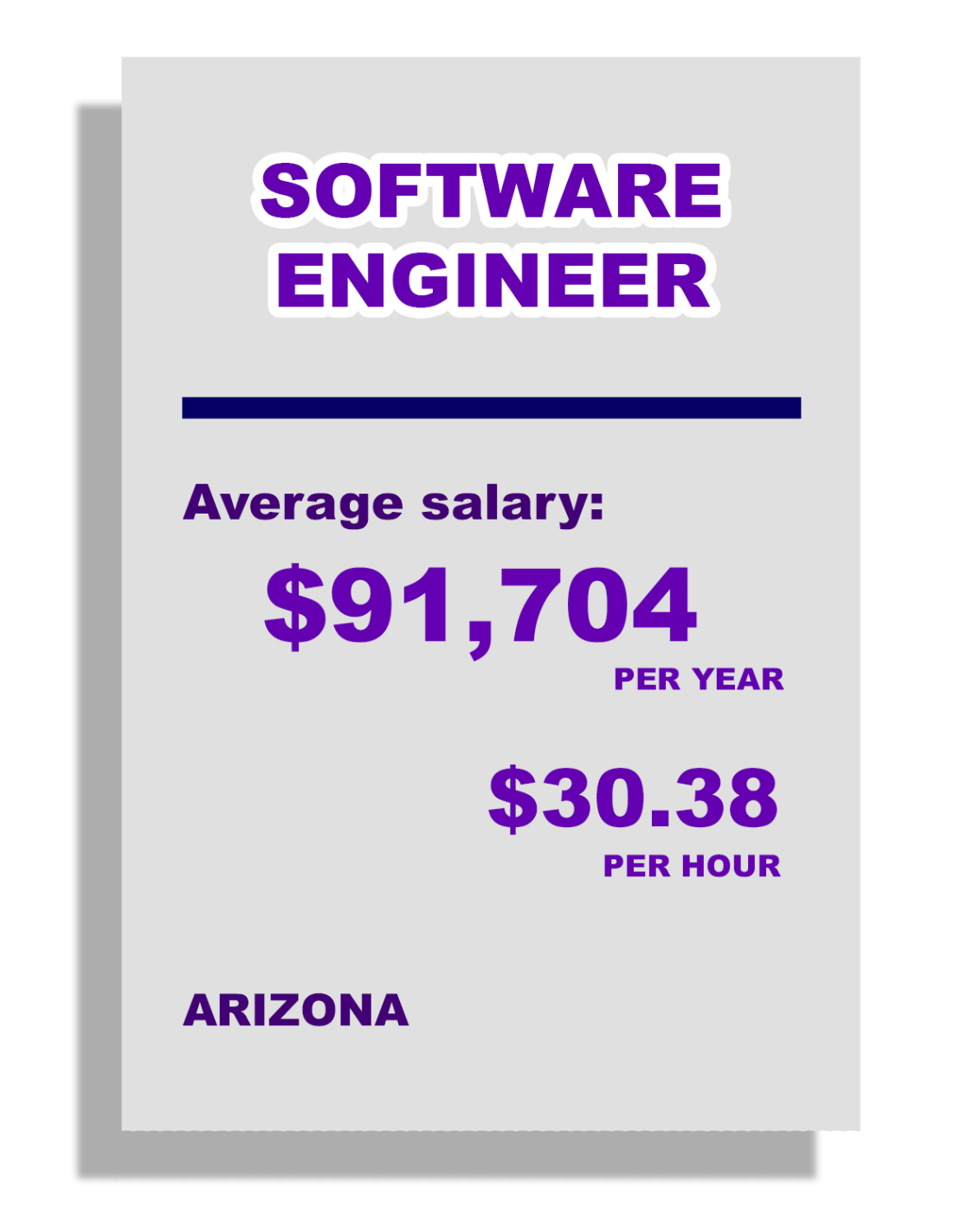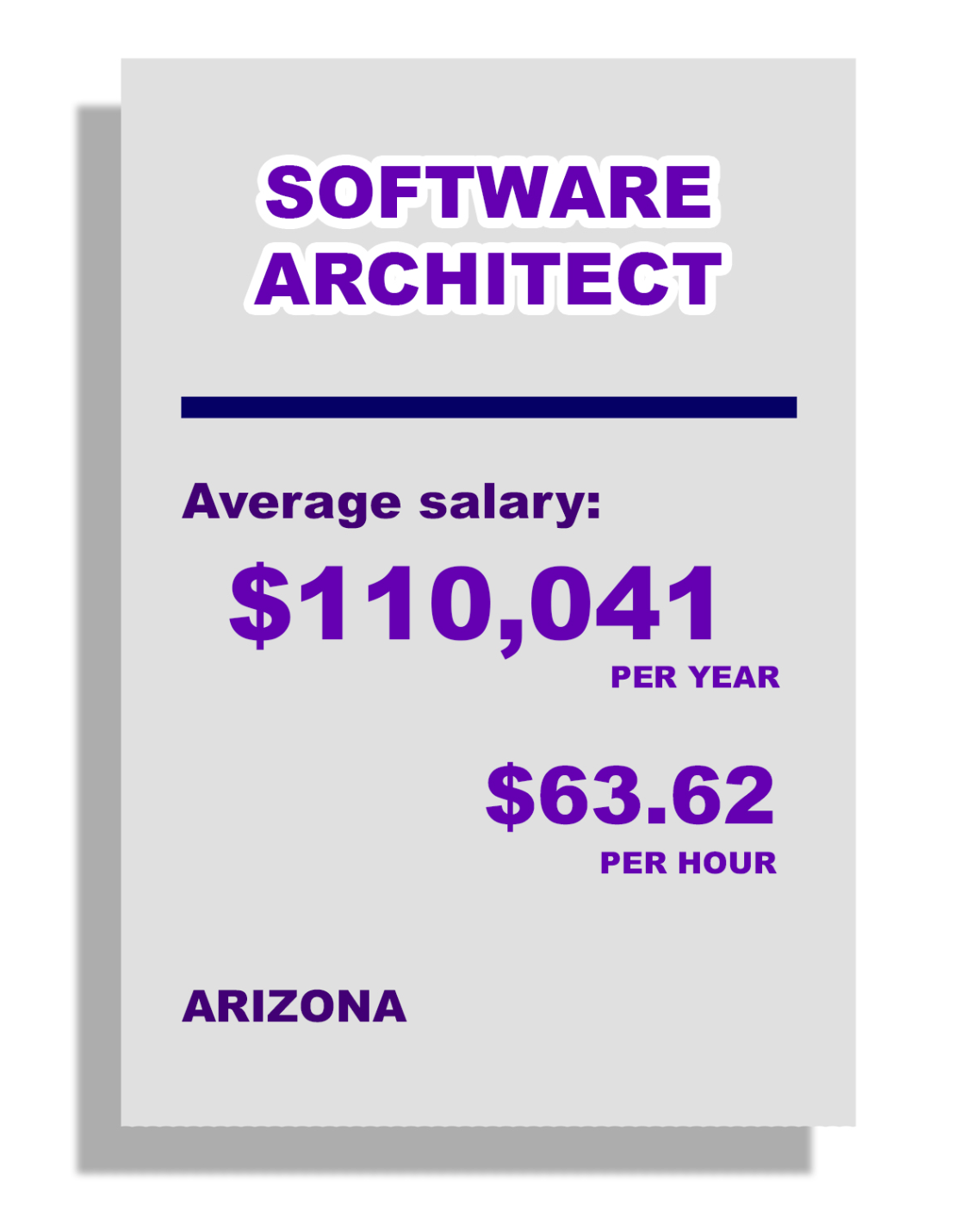


PROGRAM DESCRIPTION
Cybersecurity is an exciting, complex, and diverse field that is critical to all industries. As our lives become more dependent on internet-based tools and services, the demand for cybersecurity experience continues to expand. . In this course, we will look at, and delve into, many of the major concepts required in the field of cybersecurity. This hands-on course provides much of the foundational technical knowledge required for cybersecurity such as programming, basics of computer networking, basics of web technology, computer hardware, cryptography, secure designs of systems. Students will harden operating systems and take part in the legal/ethical issues related to cybersecurity. Students will also assess the security needs of computer and network systems, recommend safeguard solutions, and manage the implementation and maintenance of security devices. They will learn systems, and procedures to protect the property and operation of private businesses and government agencies. Students must have completed Introduction to Engineering (Engineering 1).
OFFERED AT:


IN PROGRAM PURSUITS
Here are some of the things you can look forward to while in the program:
WORK BASED LEARNING
This program and the work based learning component is being developed with our partners from Pima Community College, Raytheon and other networking and cybersecurity professionals.
PROJECTS
Building a computer
Cyber Warfare
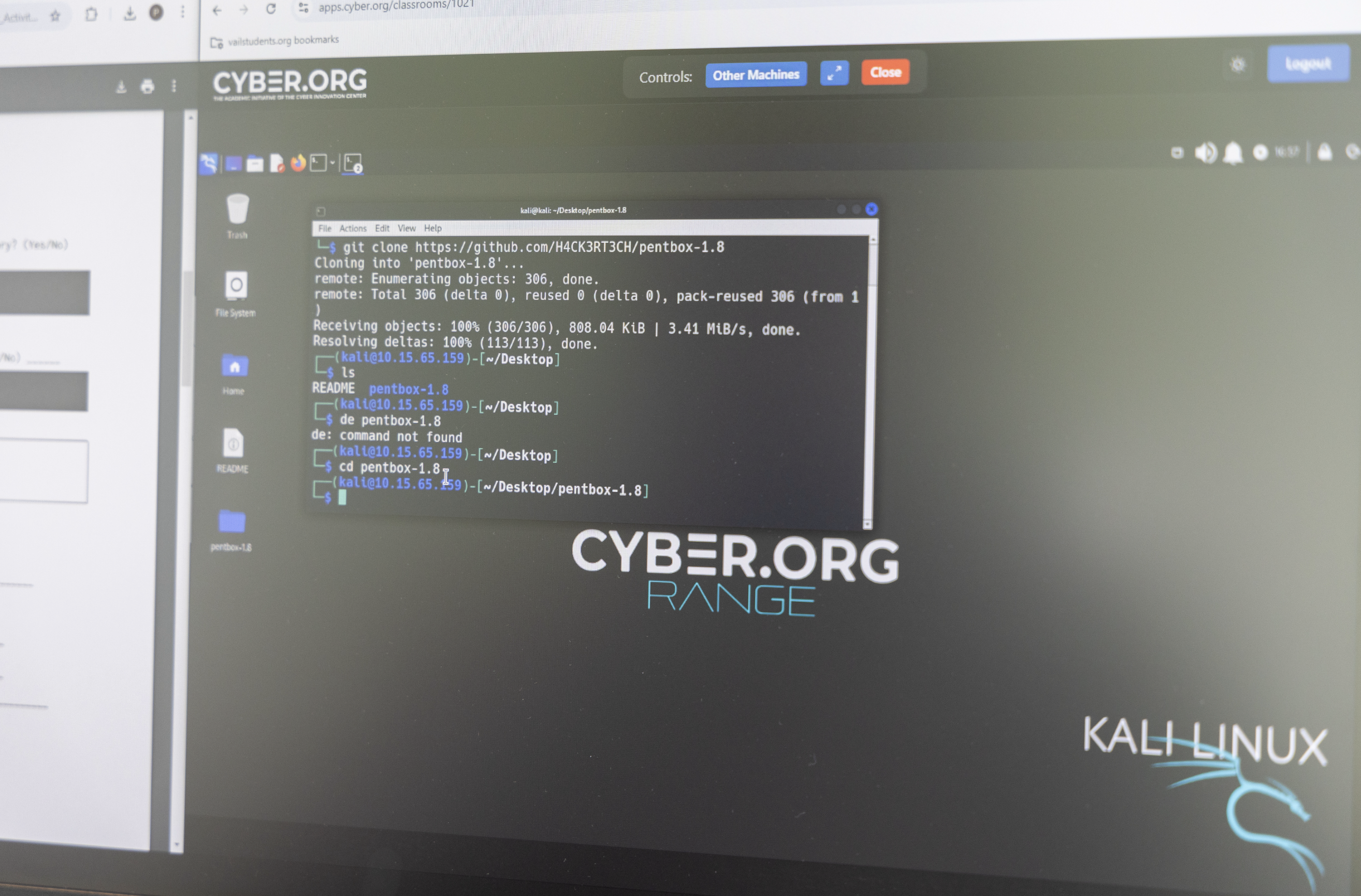
Capture the Flag activities
Install and administer computer systems and networking technologies
Problem Solving
Design Strategy and Methodology
Data Structures
Solution Analysis
Data Processing
COMPANION CLASSES
Engineering is the beginning first class to this pathway.
CLUBS & ACTIVITIES ASSOCIATED WITH PROGRAM
FBLA
CyberPatriot
CERTIFICATIONS
To Be Determined, but credentials being considered include:
CompTIA A+
Network +